| Technical Name | An Integrated Microprocessor System with Ultra Low Power Wake-up MechanismMulti-layer Hardware Security | ||
|---|---|---|---|
| Project Operator | National Cheng Kung University | ||
| Project Host | 邱瀝毅 | ||
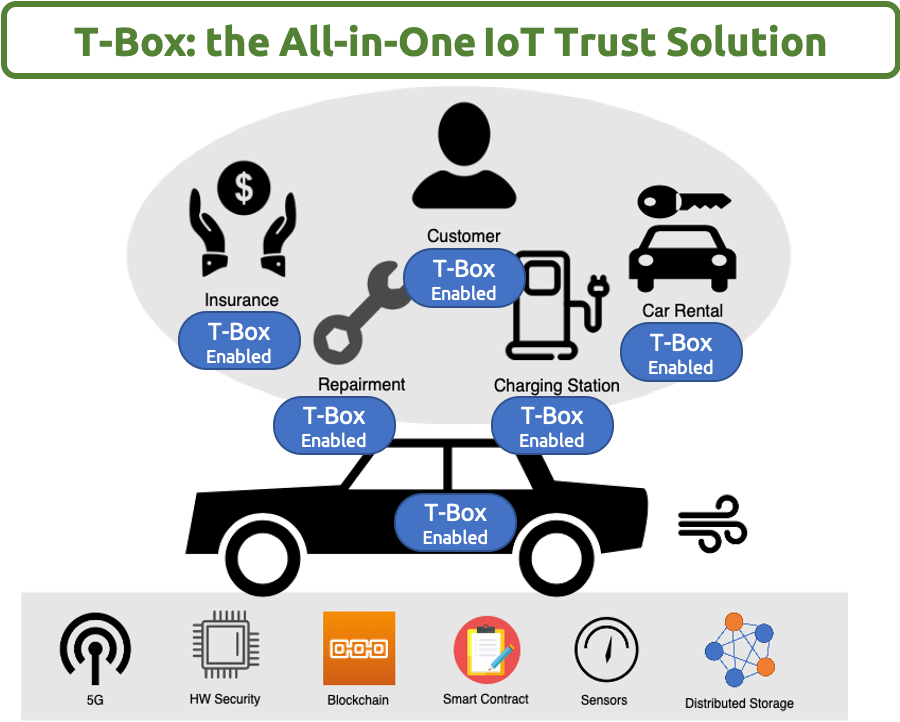
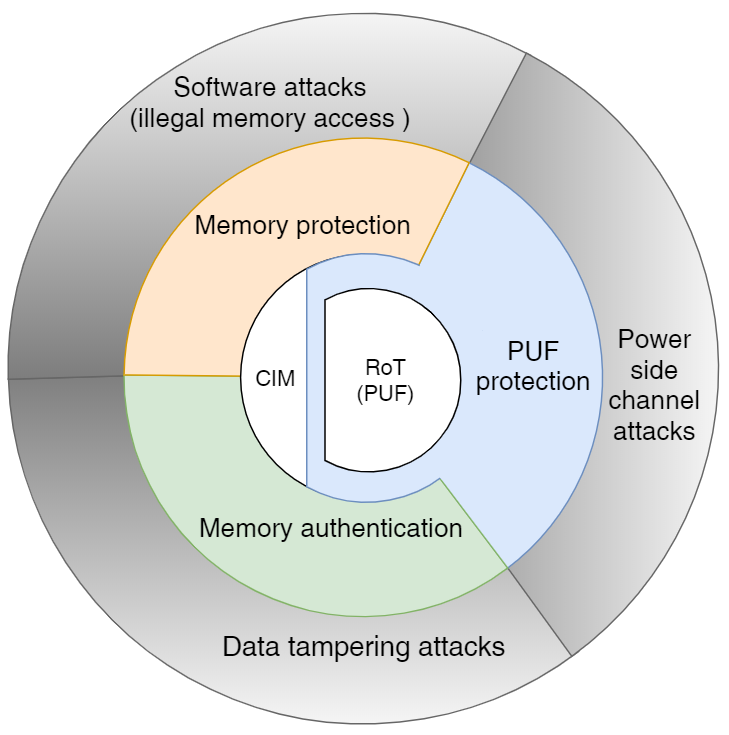
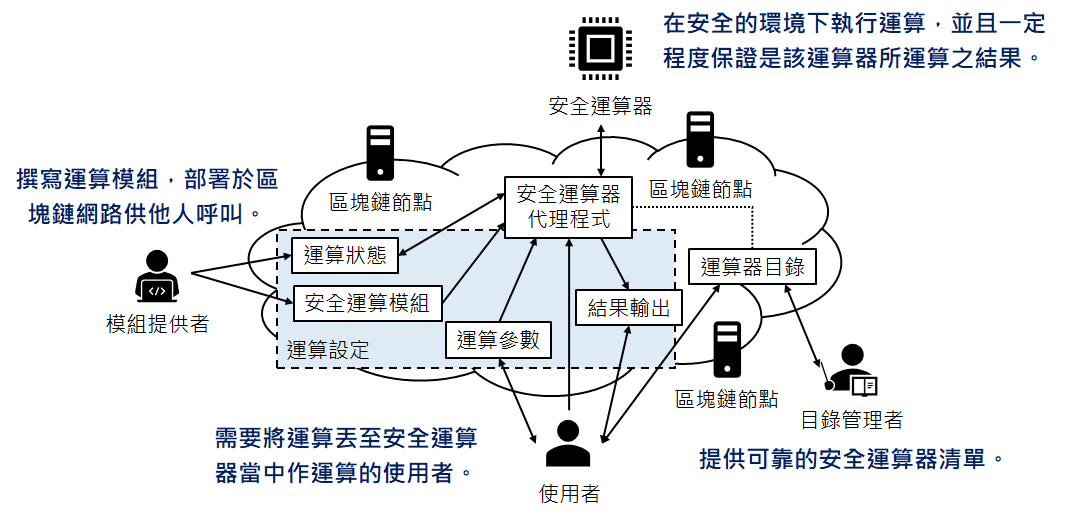
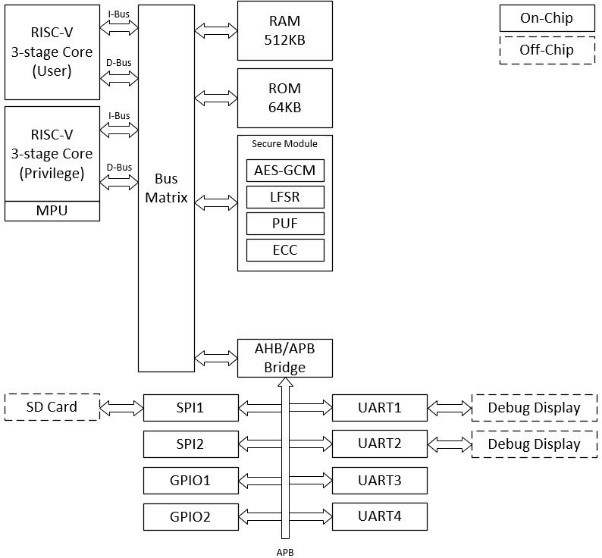
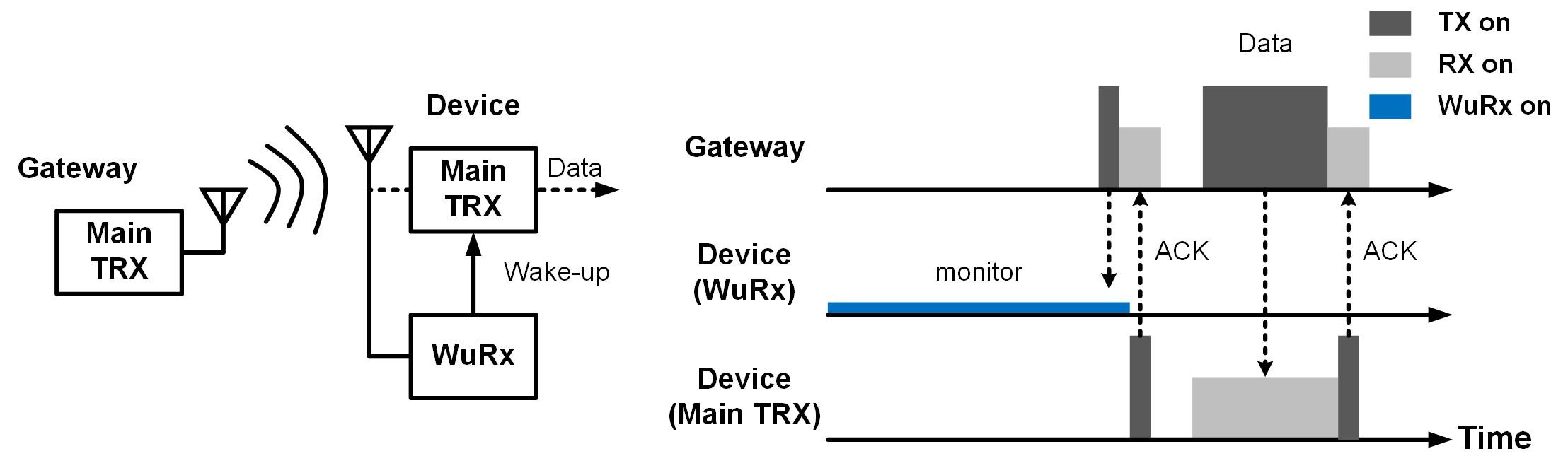
| Summary | The security processor uses the physical key as the root of trust to develop a secure boot verification process, a higher security encryptiondecryption process in the security module, etc.,can prevent malicious access to the general core, implant malicious programsSide attack. In addition, we also use memory protection mechanisms to protect confidential information. Then, by integrating a wireless transceiver with a secure wake-up mechanism, the system energy consumptioncommunication delay are reduced,a system with low power consumptionhigh security is realized. |
||
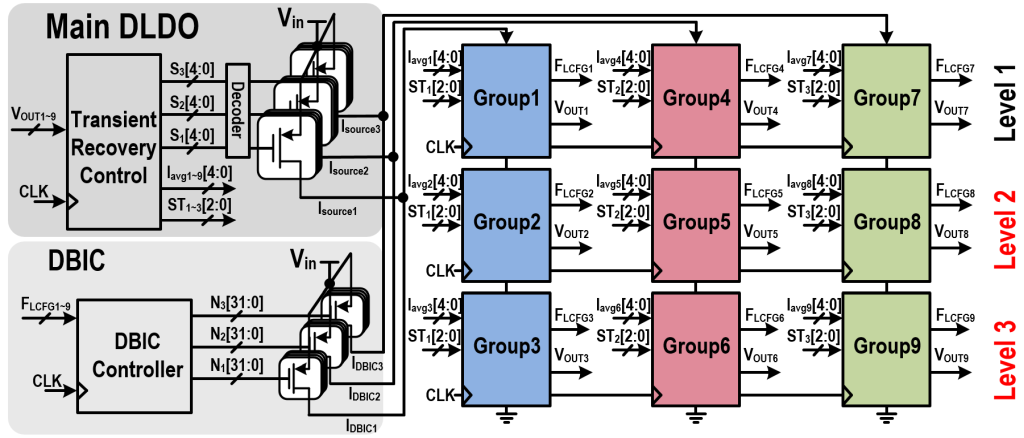
| Scientific Breakthrough | Our team independently developed a hardware multi-layer security microprocessor chip with a physical key as the root of trust, combined with a wake-up receiver, which can ensure the security of the system hardware while meeting the requirements of low power consumption,can grasp the source of intellectual propertyIncrease the system update authorityrange. |
||
| Industrial Applicability | Our team has good integration with the existing IoTsmart wearable medical application related products: the integration of security modules in hardware security facilitates technology migration,the multi-layer security mechanisms are independently developed, which can effectively control the system update authority. A wake-up receiver that supports multi-mode on low power requirementsa strict authentication mechanism with low computational requirements can prolong the battery life of the product. It is expected that the integrated system can be developed in more industrial applications. |
||
| Keyword | hardware-security physical key secure booting Encrypt/Decrypt module protection of side-channel attack low power consumption wireless sensor network wake-up receiver OOK/FSK/PSK modulation one-time wake-up pattern | ||
- Contact
- Shih-Ying Teng
- teng0984229615@gmail.com
other people also saw