| Technical Name | Protect Next-generation IoT Devices using Multi-Layer Secure Hardware | ||
|---|---|---|---|
| Project Operator | National Cheng Kung University | ||
| Project Host | 邱瀝毅 | ||
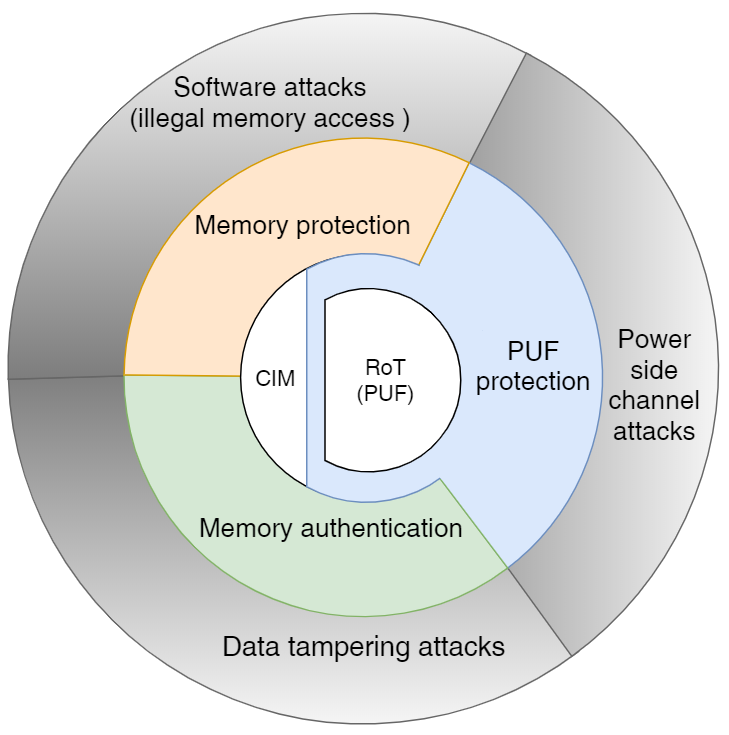
| Summary | The unclonability of PUFs makes PUFs suitable to be the root of trust of IoT devices. However, if some attackers try to rebuild the PUF model by deep learning, they can get most of the CRPs.Therefore, we should design the protection mechanisms for the PUF from the attackers.On the other hand, when executing intelligent calculations on IoT devices, by using compute-in-memory (CIM) architecture, we avoid the latency and power consumption of memory access and increase the accelerator's overall throughput. |
||
| Scientific Breakthrough | 1.Our team makes sure the security of the IoT device’s root of trust and CIM’s data through multi-layer hardware security protection mechanisms. |
||
| Industrial Applicability | Our team takes the PUF as the new proposal of root of trust, developing PUF protection mechanism, and based on the root of trust, designing a device which has multi-layer protection mechanisms and advanced accelerator containing CIM. The technology of our research results can be transferred to interested companies, providing domestic industry proper solutions. |
||
| Keyword | IoT hardware security PUF artificial intelligent CIM firmware protection root of trust side channel attack machine learning AI accelerator | ||
- N26070025@gmail.com.tw
other people also saw