prev
next
| Technical Name | Detection and Solution for Cybersecurity Threats in 4G/5G Multimedia Subsystem | ||
|---|---|---|---|
| Project Operator | National Chiao Tung University | ||
| Project Host | 謝續平 | ||
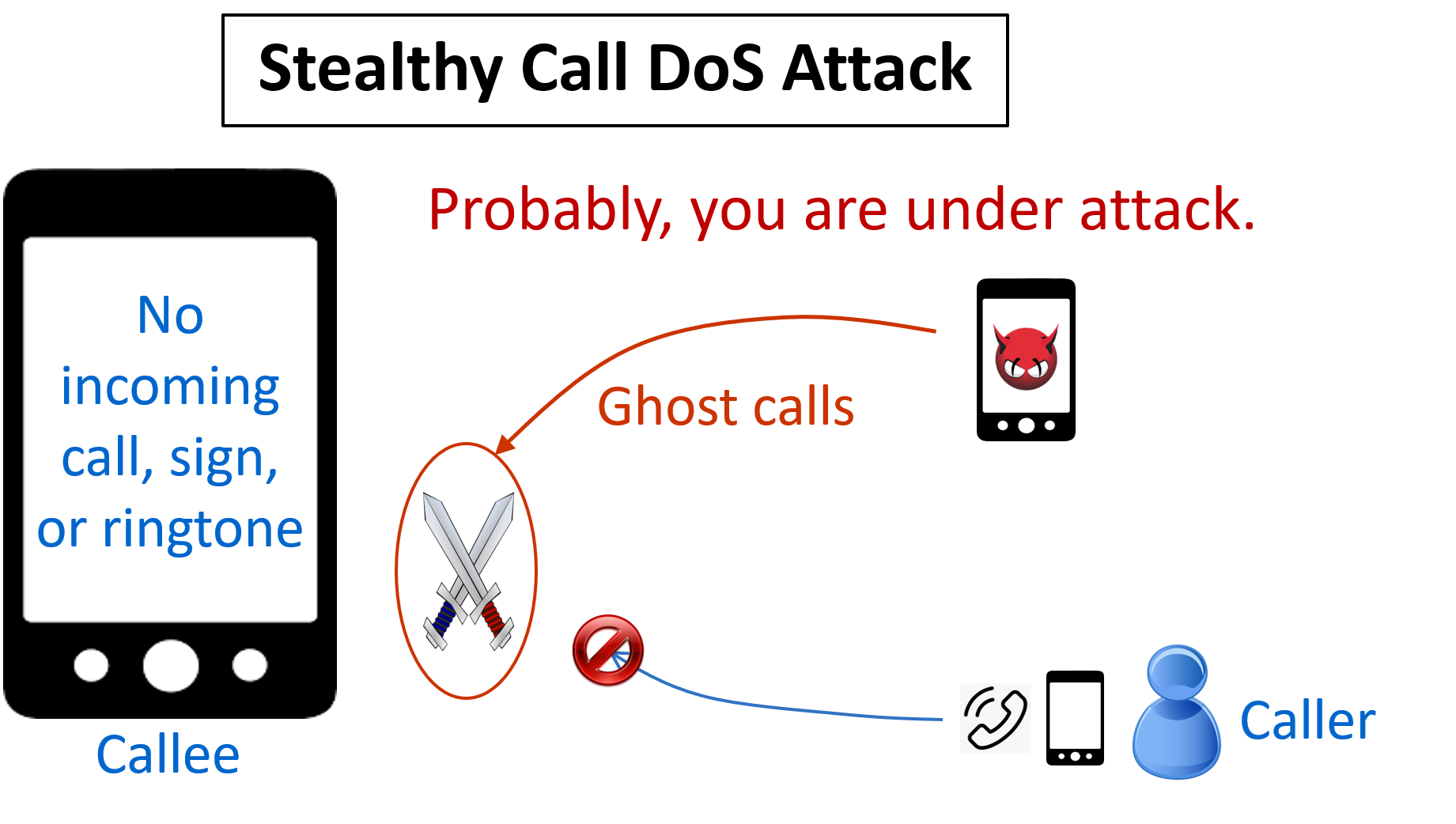
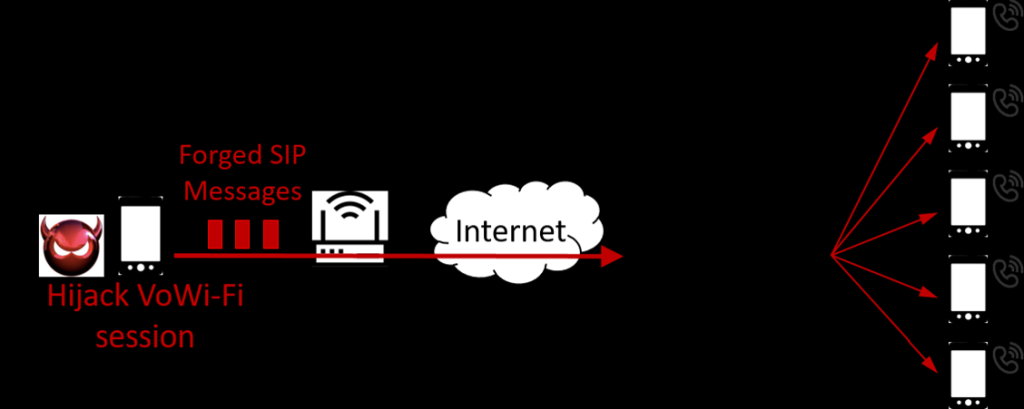
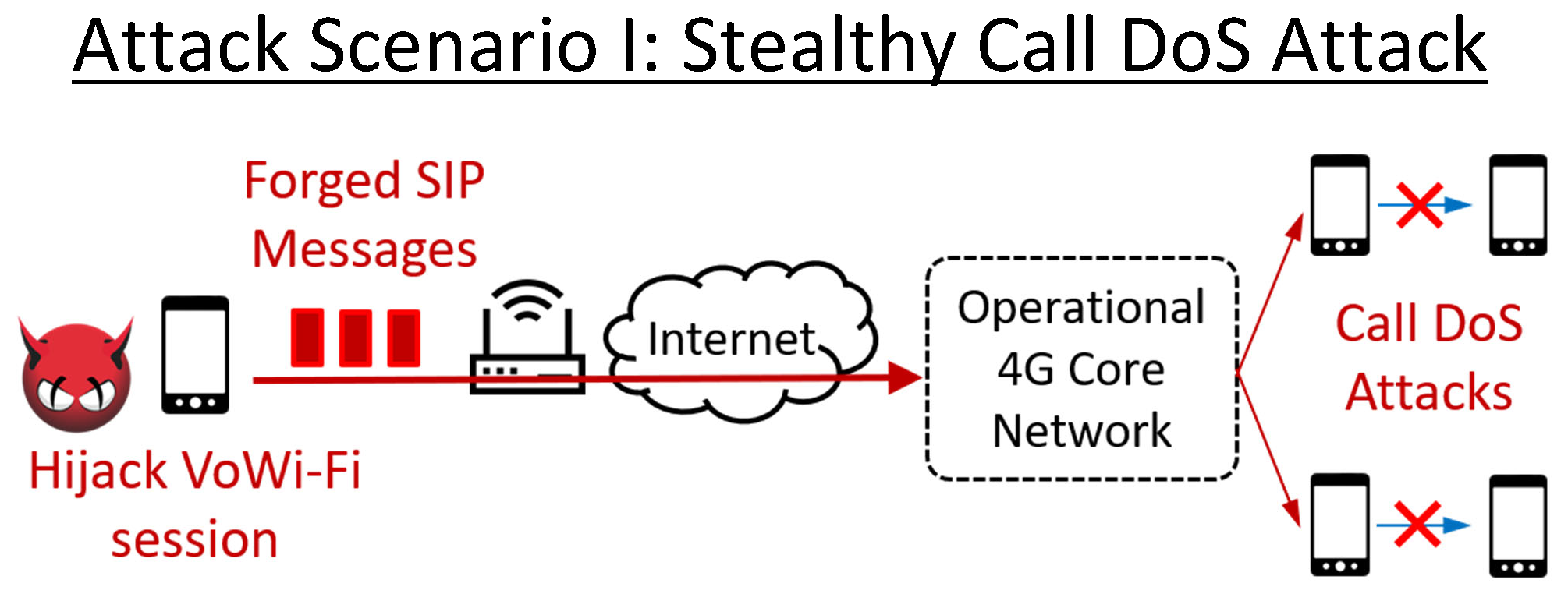
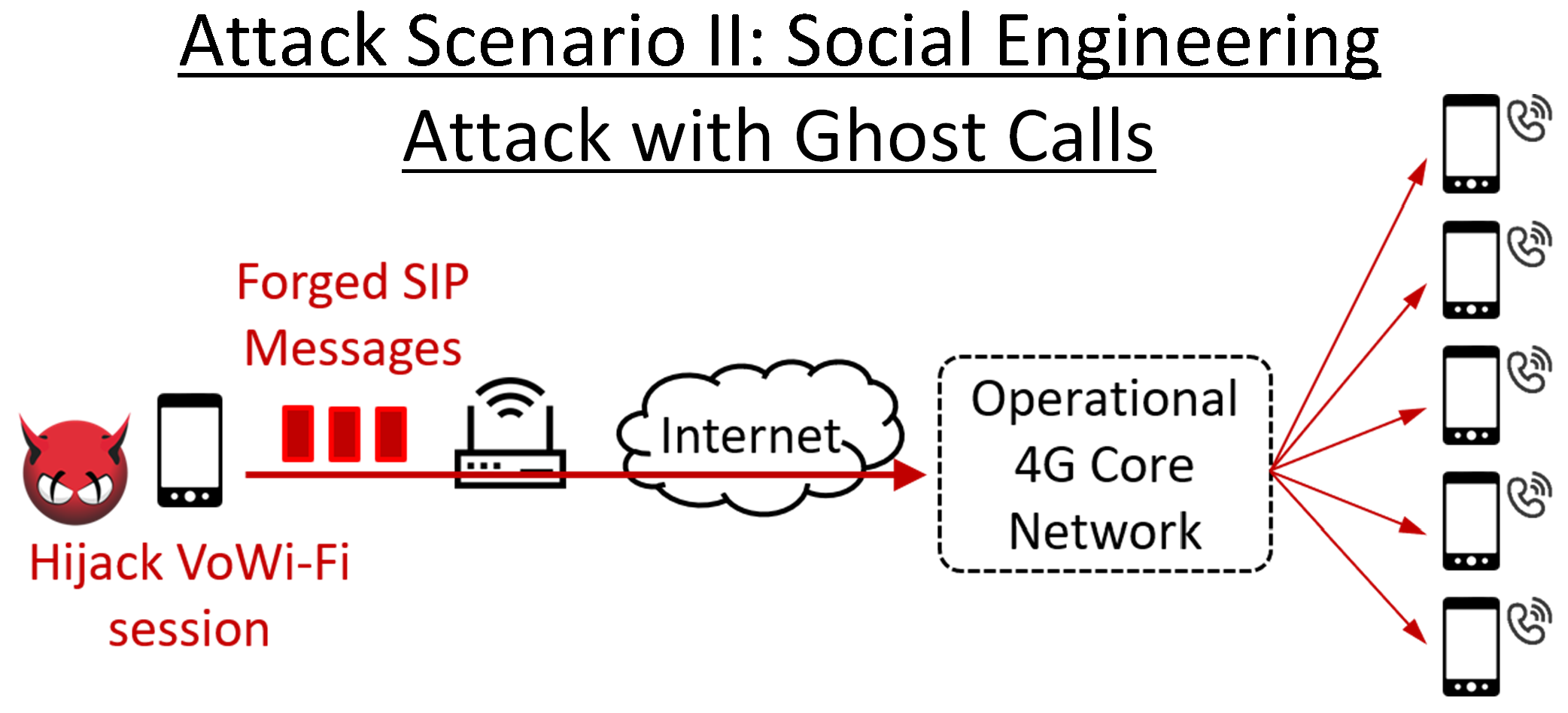
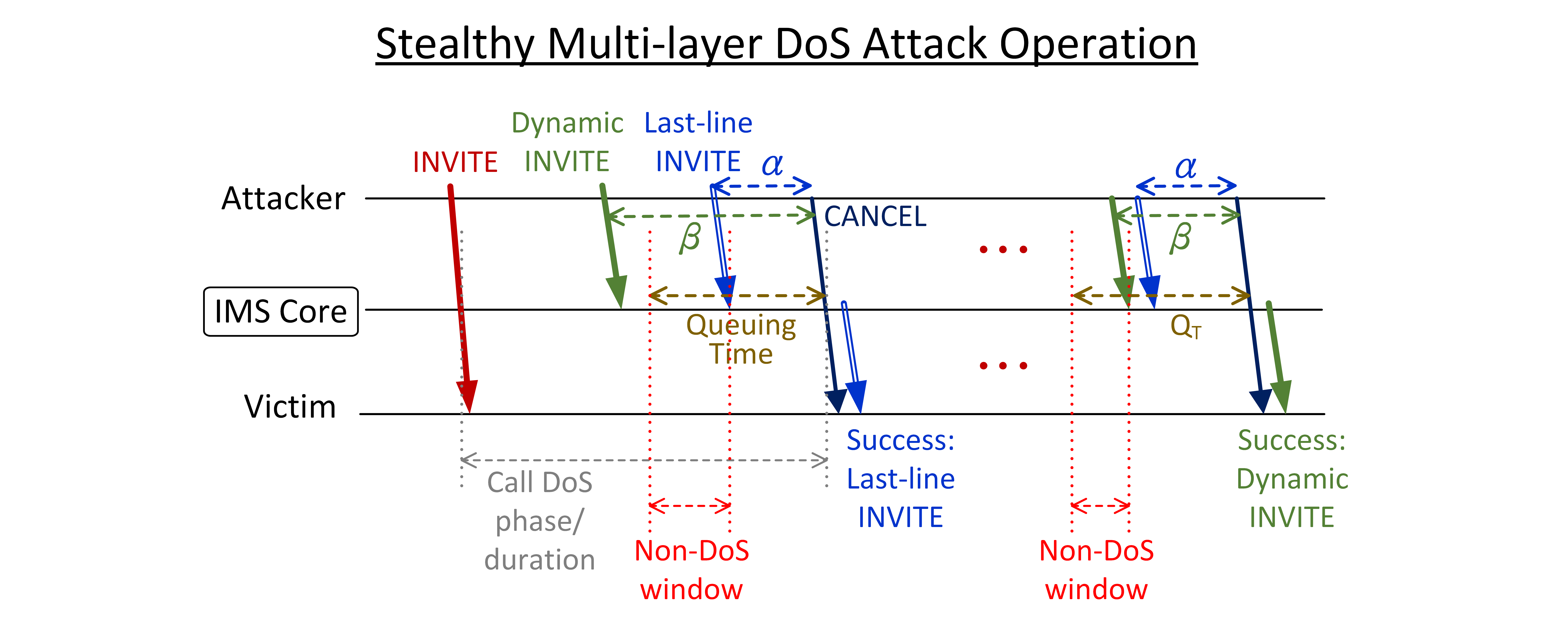
| Summary | IMS (IP Multimedia Subsystem) supports multimedia services in 4G/5G networks, so its security vulnerabilities may pose potential security threats to the 4G/5G ecosystem. We are the first group in the world to detect and identify two important security vulnerabilities in the IMS system. We have validated them in 4 carriers’ networks from Taiwan and U.S. using 7 brands’ smartphones, and also shown that they can be exploited to launch a stealthy call DoS (Denial of Service) attack and a social engineering attack with ghost calls against cellular users. In particular, the call DoS attack can prevent the cellular users from receiving or making any calls up to 99% attack time without user awareness. Moreover, attackers can detect attackable users based on a security vulnerability of the 4G network by applying our developed AI technique with only the users’ phone number. We further propose solutions and validate their effectiveness and overhead on the open-source OpenIMSCore platform. |
||
| Scientific Breakthrough | We are the first group in the world to make the following four achievements. |
||
| Industrial Applicability | The security threats identified by us generally exist in global 4G/5G cellular network systems. Their root causes lie in design flaws of network protocols, defects of network operations, or insecure app implementations. Our developed technologies can assist cellular network standards, carriers, and telecom/phone vendors in detecting and addressing the security vulnerabilities of 4G/5G cellular networks and multimedia services. They can be contributed to the security protection of the 4G/5G ecosystem for the global telecom industry. |
||
| Keyword | Cyber security network security cellular network IMS IP Multimedia Subsystem 4G 5G VoLTE VoWiFi 5G security | ||
- cchingyi@nctu.edu.tw
other people also saw
prev
next