| Technical Name | TBox: All-in-One IoT Trust Solution | ||
|---|---|---|---|
| Project Operator | National Taiwan University | ||
| Project Host | 林宗男 | ||
| Summary | Next-gen IoT applications are faced with even more severe cybersecurity challenges than ever. TBox to the rescue! |
||
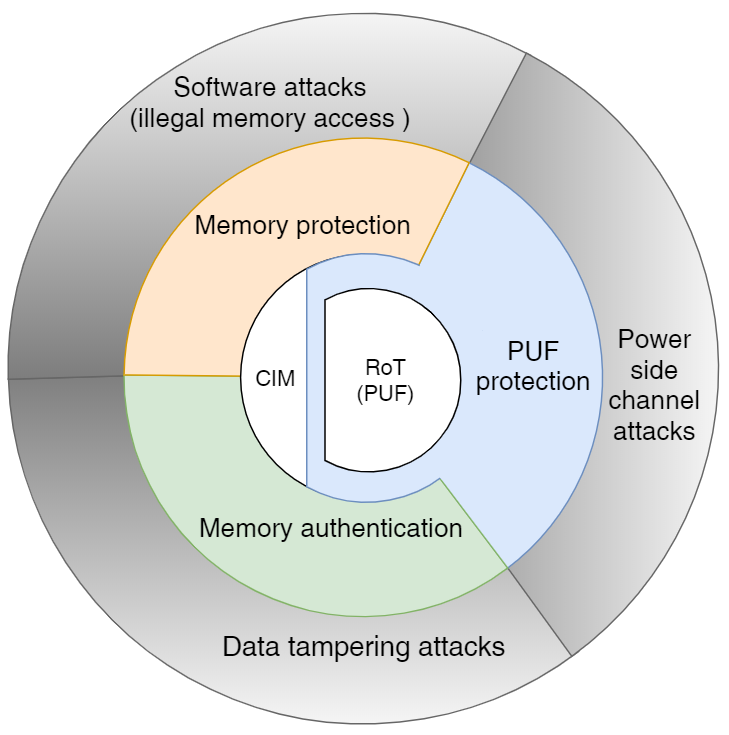
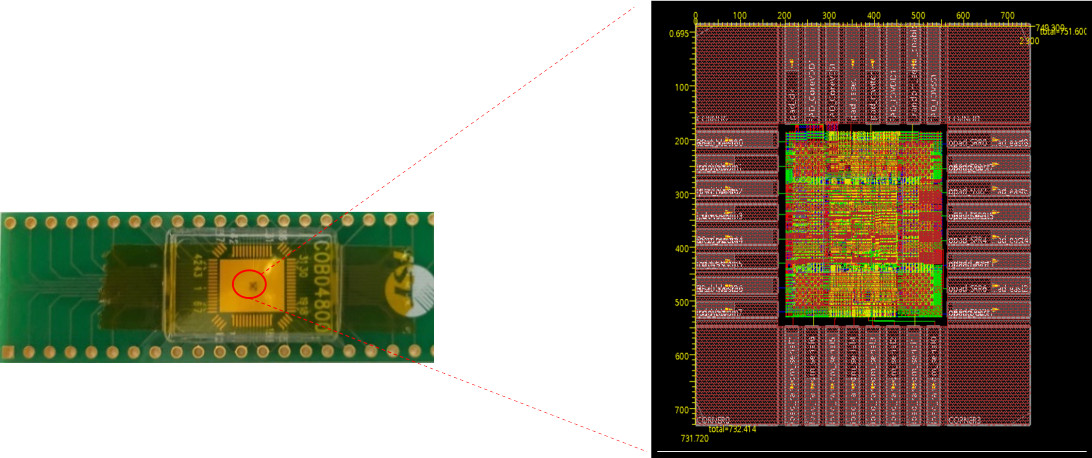
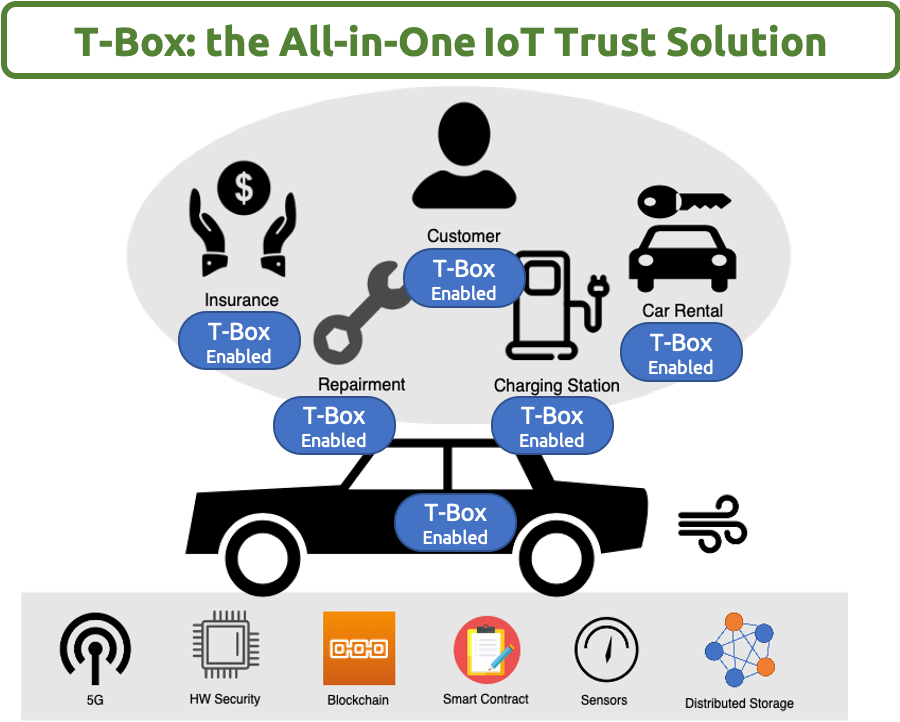
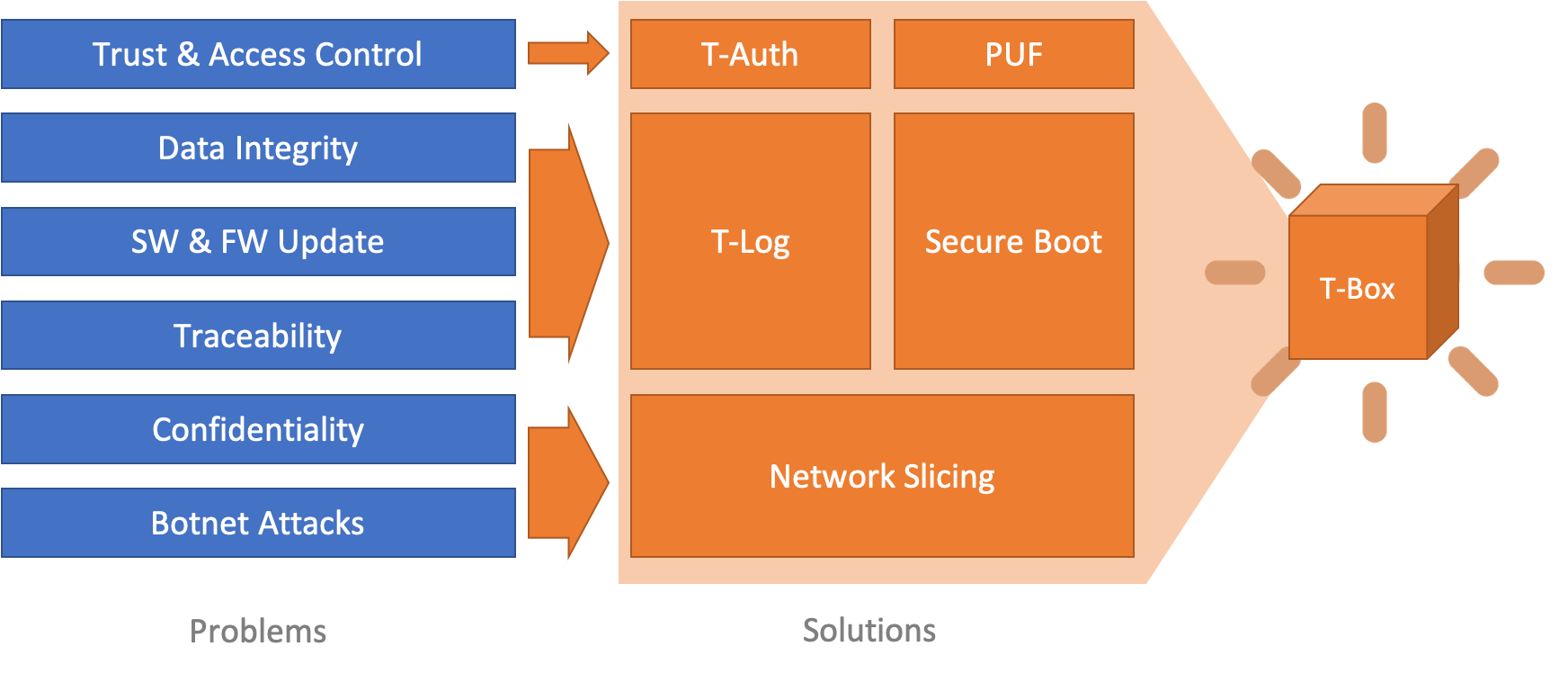
| Scientific Breakthrough | TBox adopts PUF-based digital fingerprinting mechanism to give device a unique and unclonable identity. Based on this root-of-trust, we developed blockchain-based authentication, access control and provenance mechanisms along with network slicing techniques to provide “trust” for IoT devices. All the novel technologies jointly support TBox-enabled devices to form a decentralized secured network together. |
||
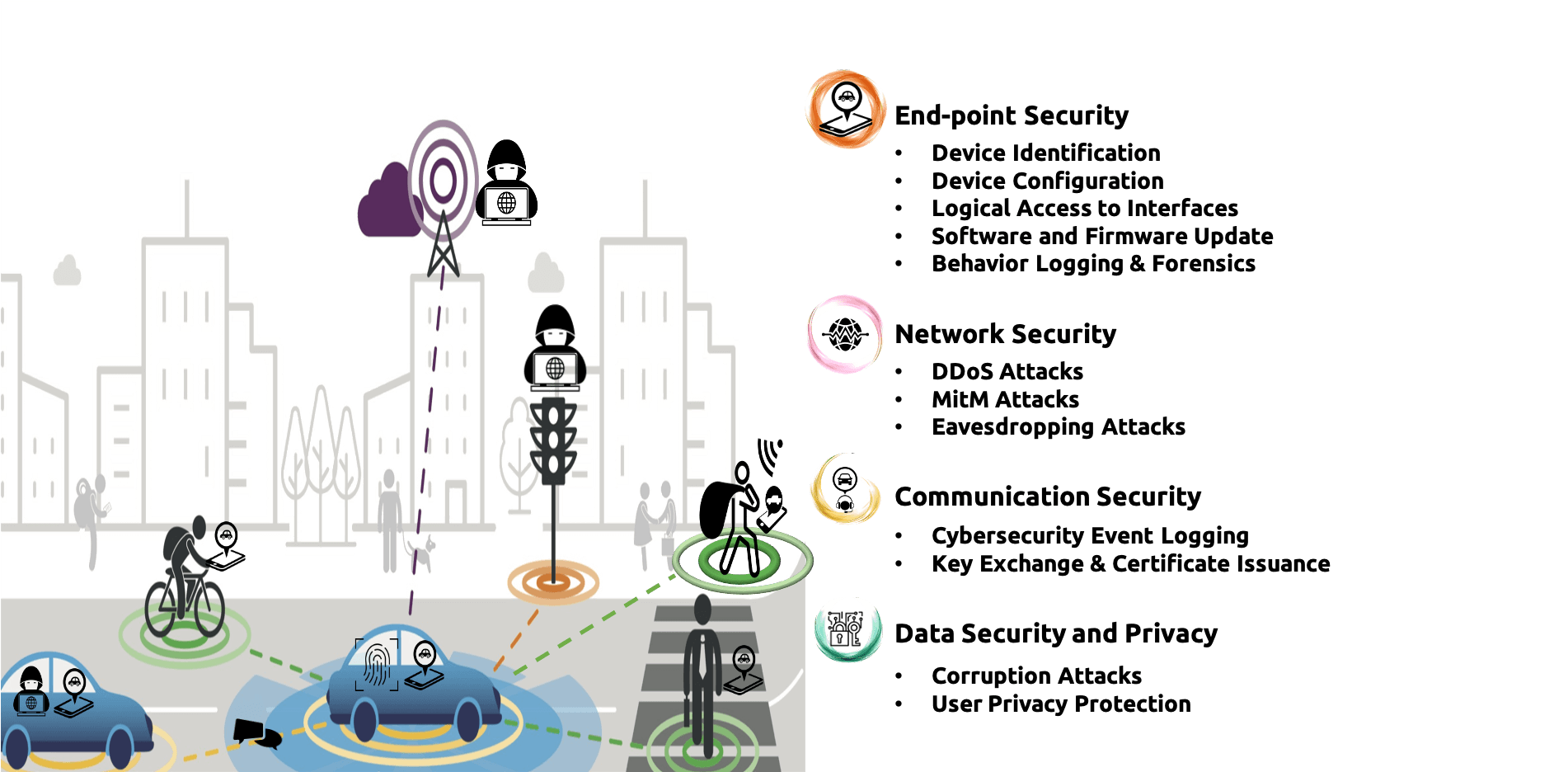
| Industrial Applicability | Starting from 2020, new laws and standards published by US, Europe and other countries around the world are paying more attention to activities related to IoT security. The acts and standards explicitly place the responsibility of securing devices on manufacturers and designers instead of end users. The trend urges product developers to face the ever-increasing security threat. By taking care of issues arising from end-point, network, communication and data aspects, TBox provides an all-in-one trust solution that enables connected vehicles, intelligent logistics, healthcare and smart factory applications to work safely. |
||
| Keyword | IoT Internet of things Cyber security 5G Blockchain PUF Hardware Network Communication Decentralized | ||
- huangyuping@ntu.edu.tw
other people also saw