prev
next
| Technical Name | Industrial Control System Transmission Protection System | ||
|---|---|---|---|
| Project Operator | National Cheng Kung University | ||
| Project Host | 李忠憲 | ||
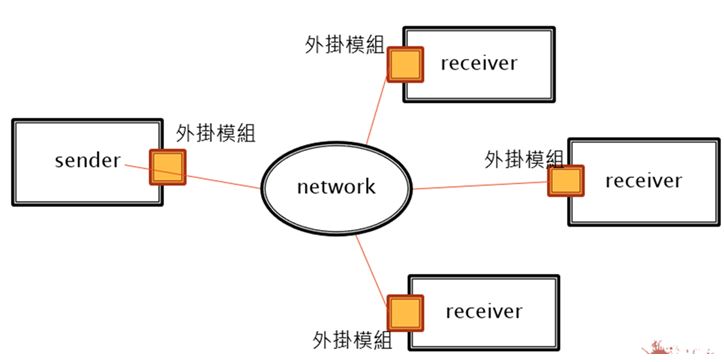
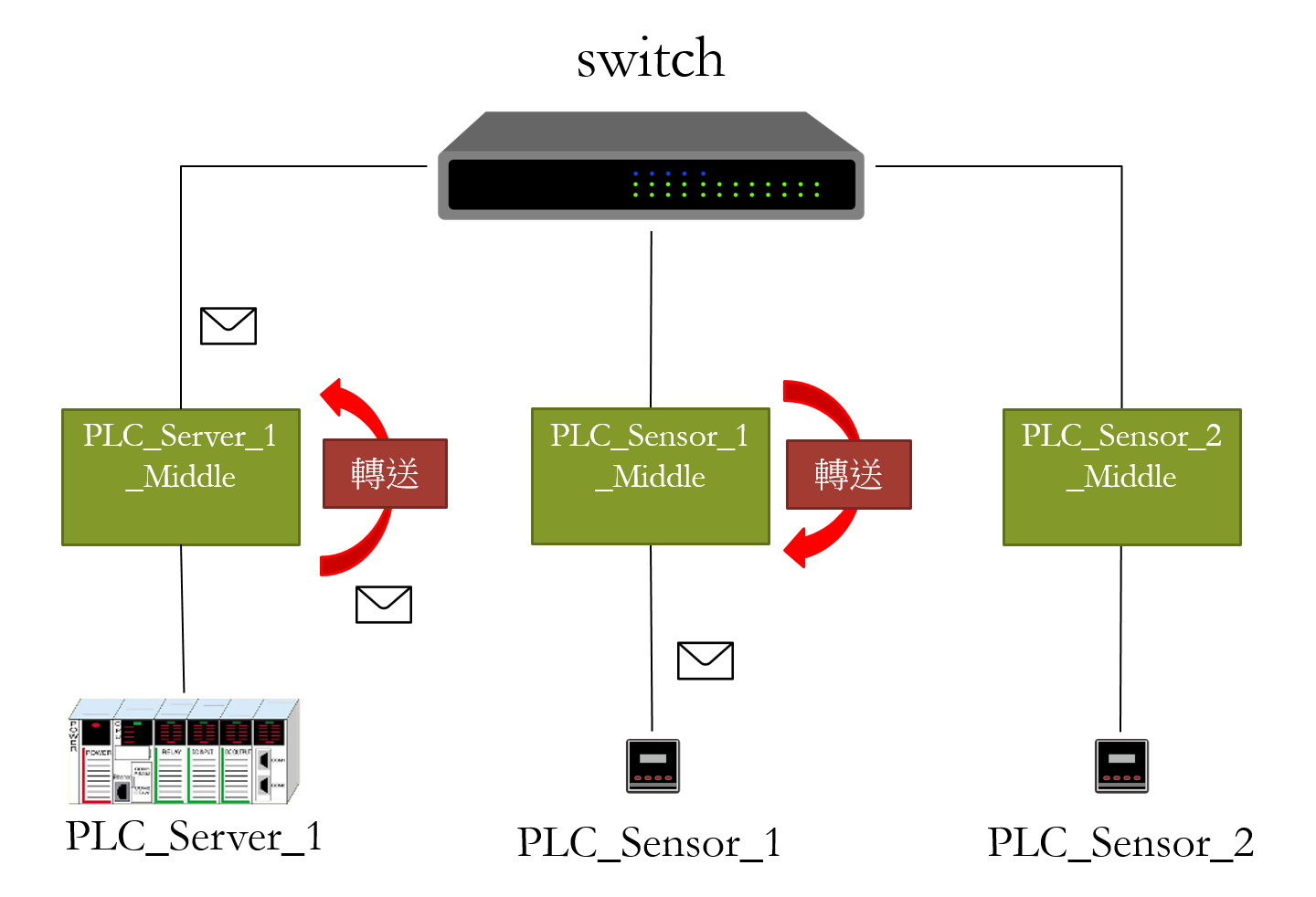
| Summary | The reason why communication can let the two parties know what messages are sent between each other is that the two parties have a common protocol, communication approach (including encryption and decryption), and the location of communication with each other. Our proposes a new protection mechanism that allows the two parties to continuously change the communication addresses of the sender and the receiver on the existing basis, to ensure that the addresses of both parties are only known by the two parties and that each time the communication can be successfully completed. In addition, we dynamically change the address of the next communication and block the related attacks and security risks by illegal communicators unable to obtain the correct address. |
||
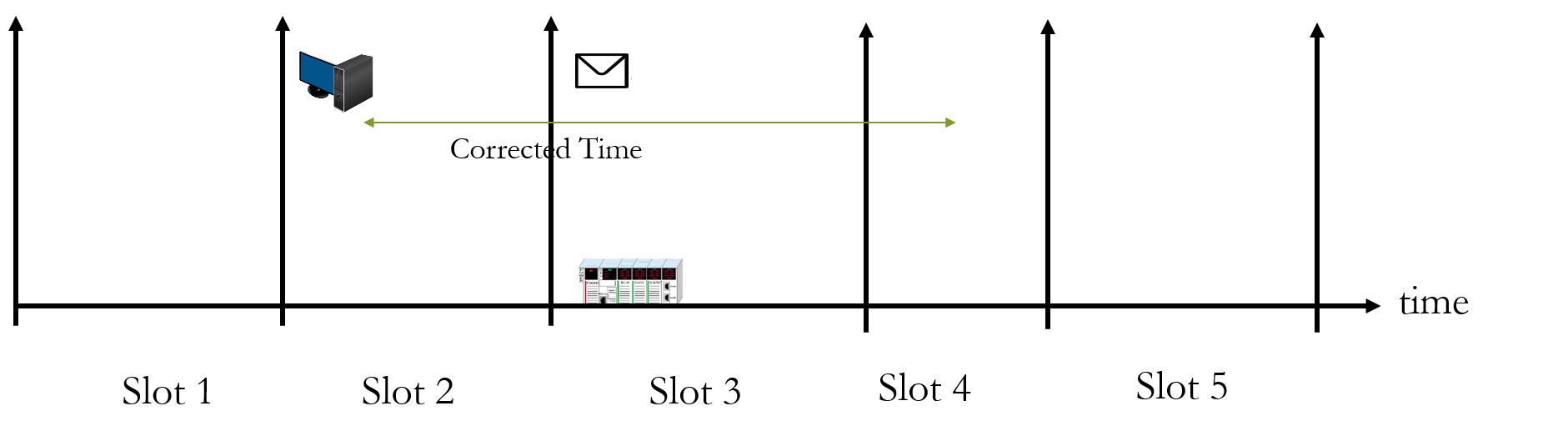
| Scientific Breakthrough | The advantage of moving target defense (MTD) is that it can make hackers encounter difficulties at the reconnaissance stage. However, there are still many problems with the existing moving target defense technology. After changing the address, another can not know the address to be communicated, or when they notify the address to others may be intercepted by the hacker to obtain the address. Finally, the time-based moving target defense has time synchronization problems, such as MT6D. So we have made improvements to these problems, using both parties to calculate the next communication address, the transmission process will not send out the addresses of both parties, and they know what each address is. then also correction time synchronization problems. |
||
| Industrial Applicability | Most of the existing industrial control systems (ICS) use the Modbus protocol, but the Modbus protocol is not encrypted. Therefore, the attacker can send commands to the device by sending Modbus packets, so this study uses dynamic addressing to communicate, and dynamically changes and calculates whether the requested address is legal. In this way, the attacker cannot find the address of the device and cannot perform the attack. Therefore, if dynamic addressing is applied to the security of the ICS, it can add a layer of authority and this method does not need to modify the protocol of ICS, we only need to install the dynamic addressing device on the system. In this way, the hacker will encounter difficulty at the reconnaissance stage. |
||
| Keyword | Communication Moving target defense Security Dynamic addressing Critical infrastructure protection Connectionless addressing defense MTD Connection | ||
- ihliu@twisc.ncku.edu.tw
other people also saw
prev
next