| Technical Name | An Automated IoT Malware Sandbox with Emulated Hardware Architectures | ||
|---|---|---|---|
| Project Operator | Taiwan Information Security Center of National Taiwan University of Science and Technology | ||
| Project Host | 鄭欣明 | ||
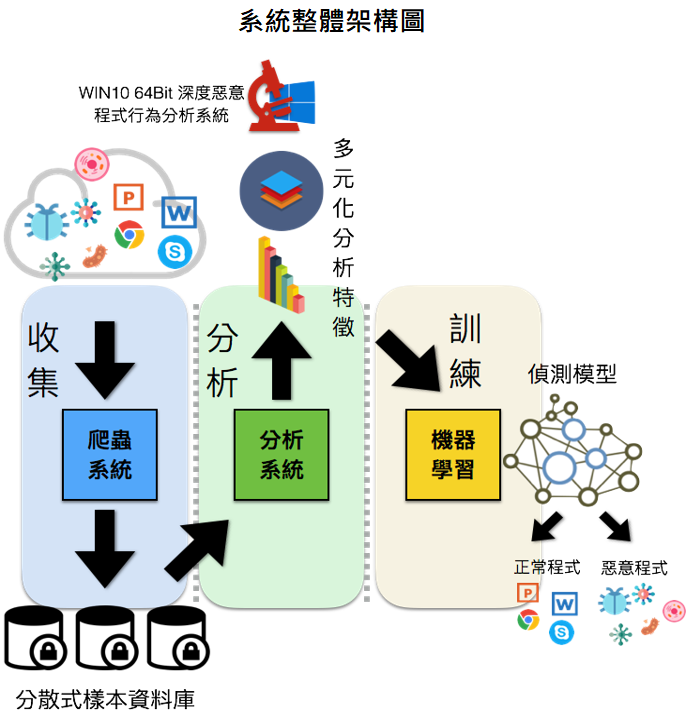
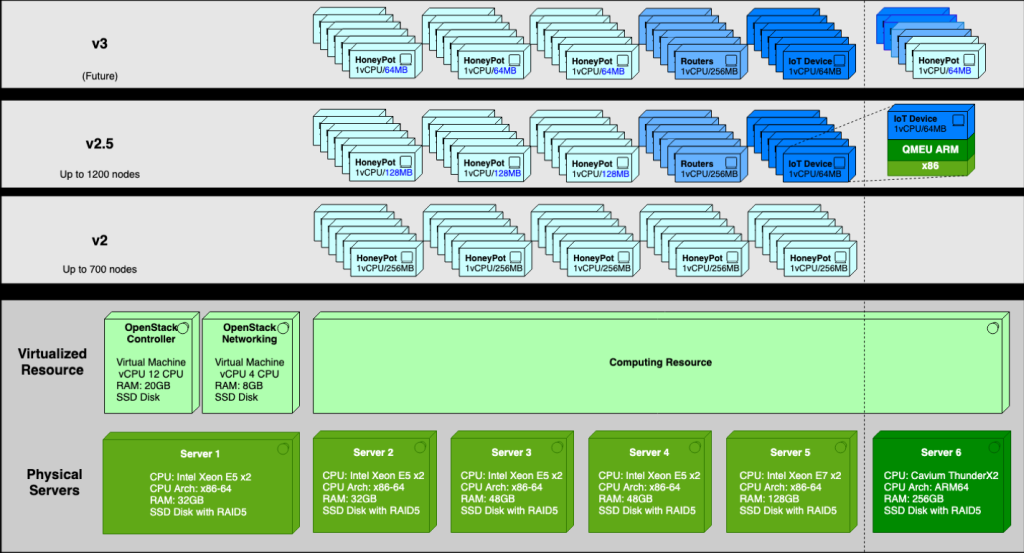
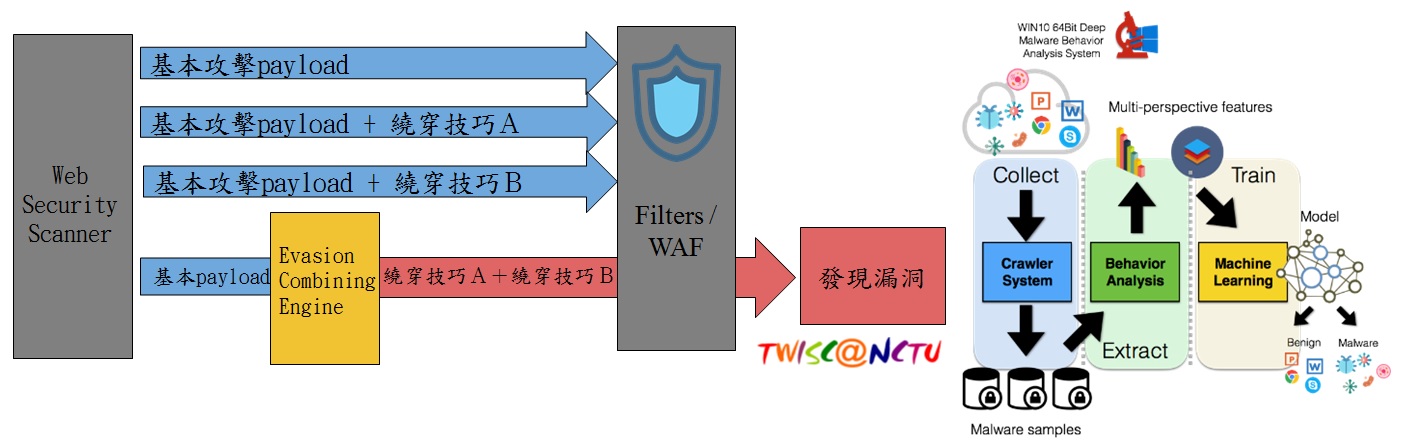
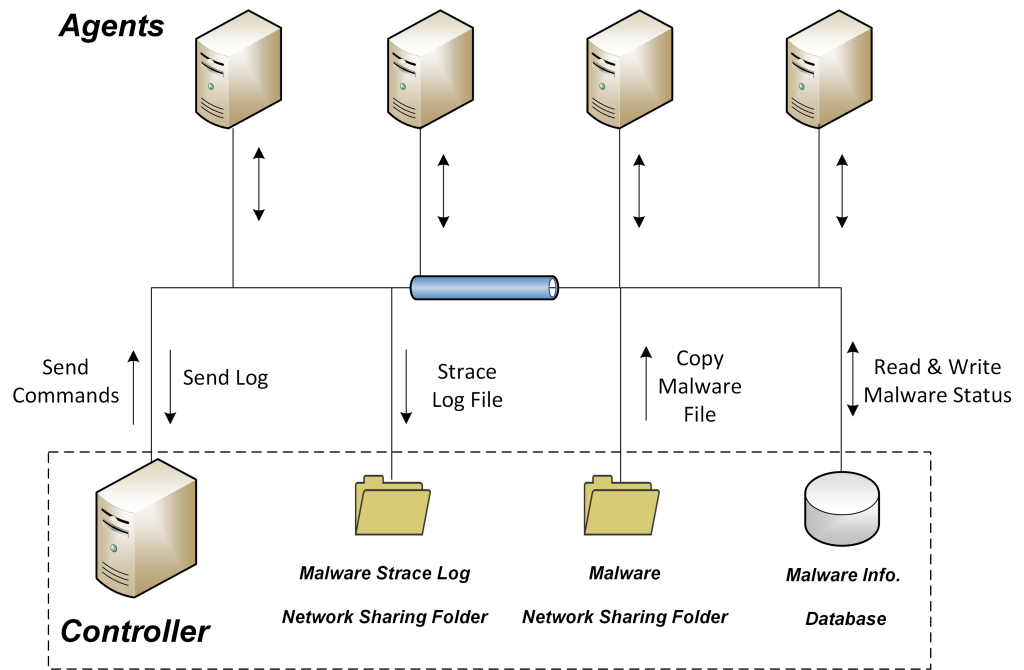
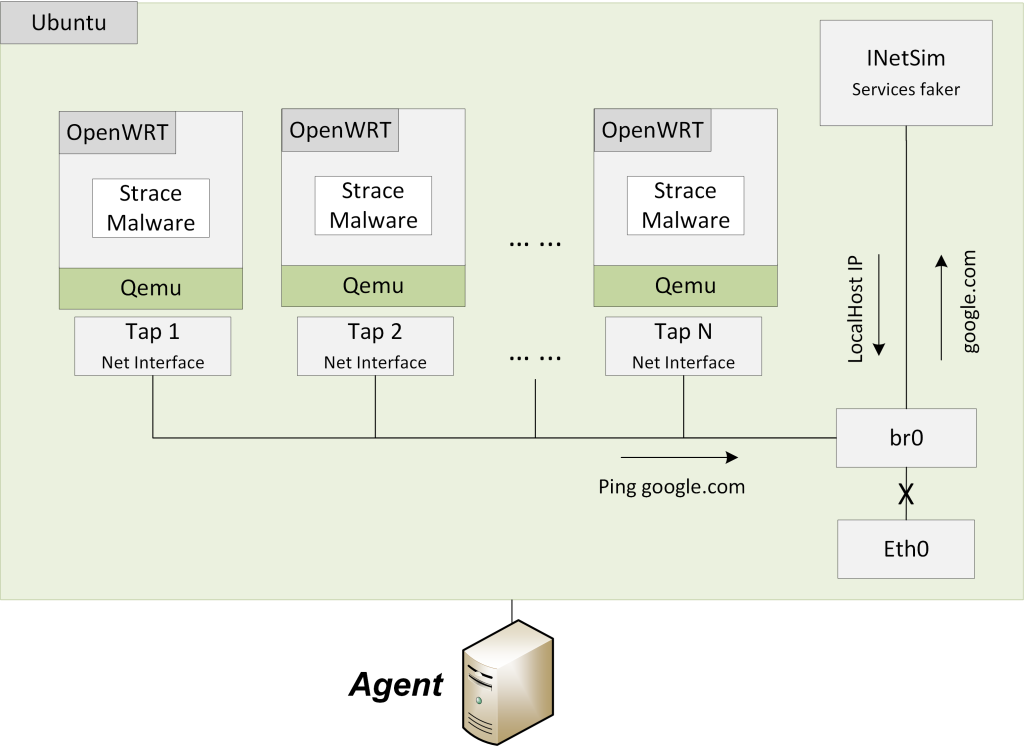
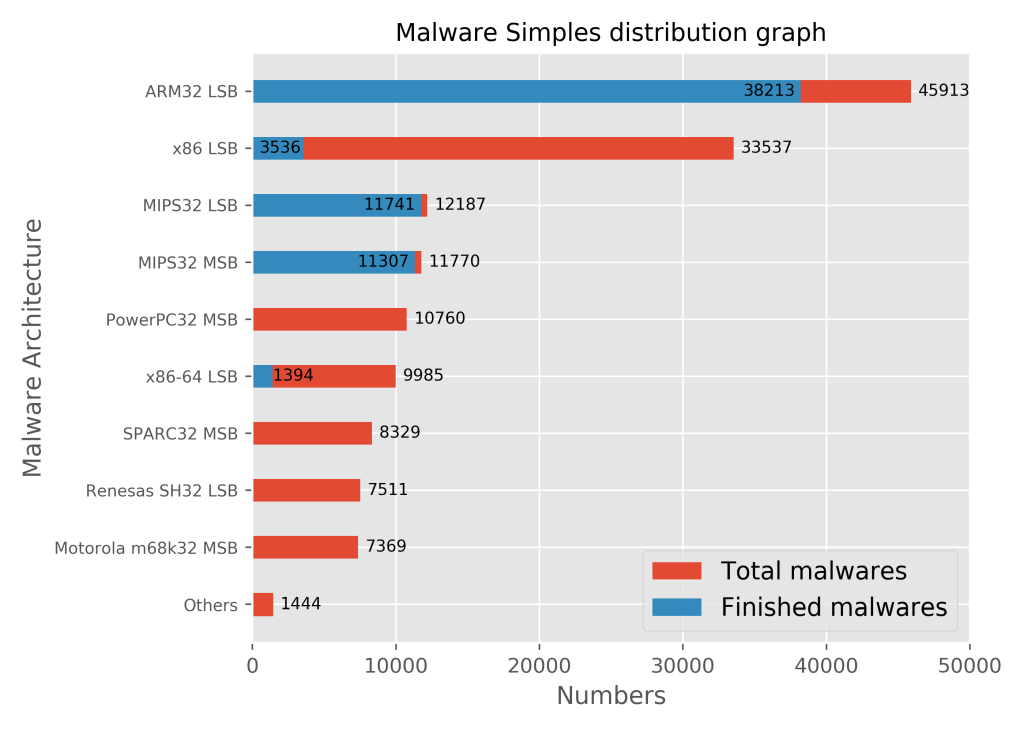
| Summary | An analysis IoT sandbox based on strace is build, which supports a set of QEMU-based emulated sandboxes for ARM32, x86, MIPS, PowerPC, x86-64, SPARC, and aarch64. The execution of 147,630 malware simples from VirusTotal inside the emulator results in the full trace of system calls. The generated dataset can be the foundation for more systematic future works for IoT malware detection, and defense. |
||
| Scientific Breakthrough | We include strace function into ARM32, x86, MIPS, PowerPC, x86-64, SPARC, and aarch64 environment emulated by using QMEU, thereby analyzing malware with a much wider range of architectures than the existing sandbox. |
||
| Industrial Applicability | IoT malware introduces tremendous threats to the industry who uses legacy IoT devices or develops future IoT products. The dataset generated from the sandbox details the processing behavior of a large number of IoT malwares with different CPU architectures. By analyzing the dataset, the security investigation and secure development of IoT products for the industry can be profoundly facilitated. |
||
| Keyword | Architecture emulation ARM Dataset generation Dynamic analysis IoT malware MIPS QEMU Sandbox System call VirusTotal | ||
- ycwlove1@gmail.com
other people also saw