| Technical Name | Malware Classification System based on Artificial Intelligence and Correlation Rules | ||
|---|---|---|---|
| Project Operator | TWISC@NCKU | ||
| Project Host | 李忠憲 | ||
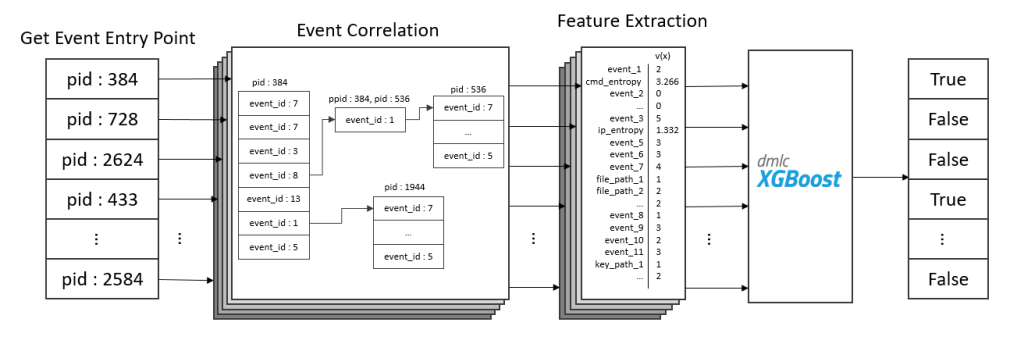
| Summary | Different from the researches that using the signature based detection system, the proposed system used the correlation rules to analyze host log. When faced with malware that concealed in different processes, network managers can use a more comprehensive perspective to analyze the attack. |
||
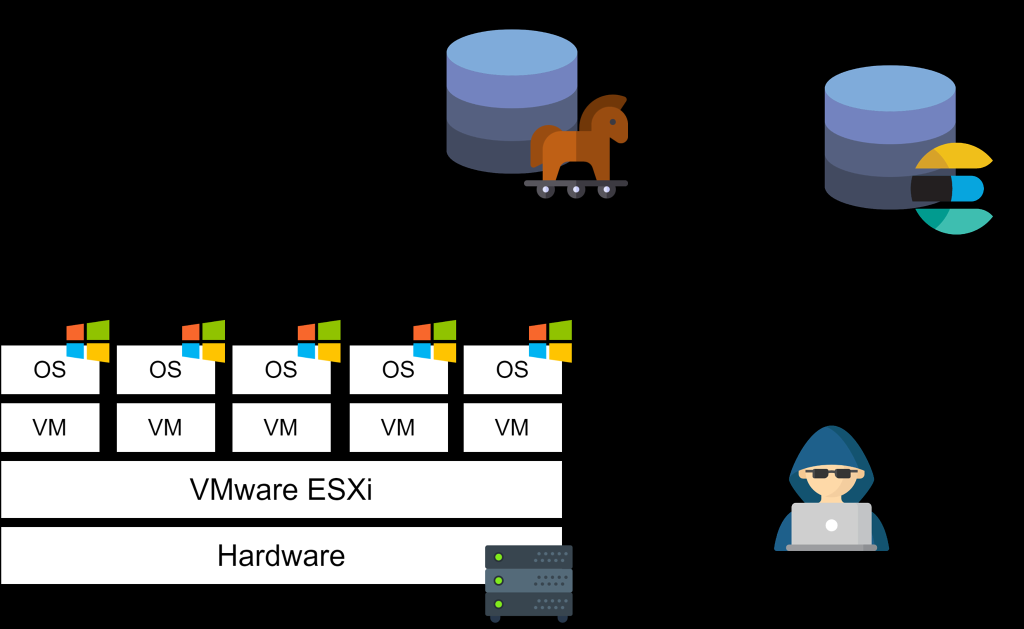
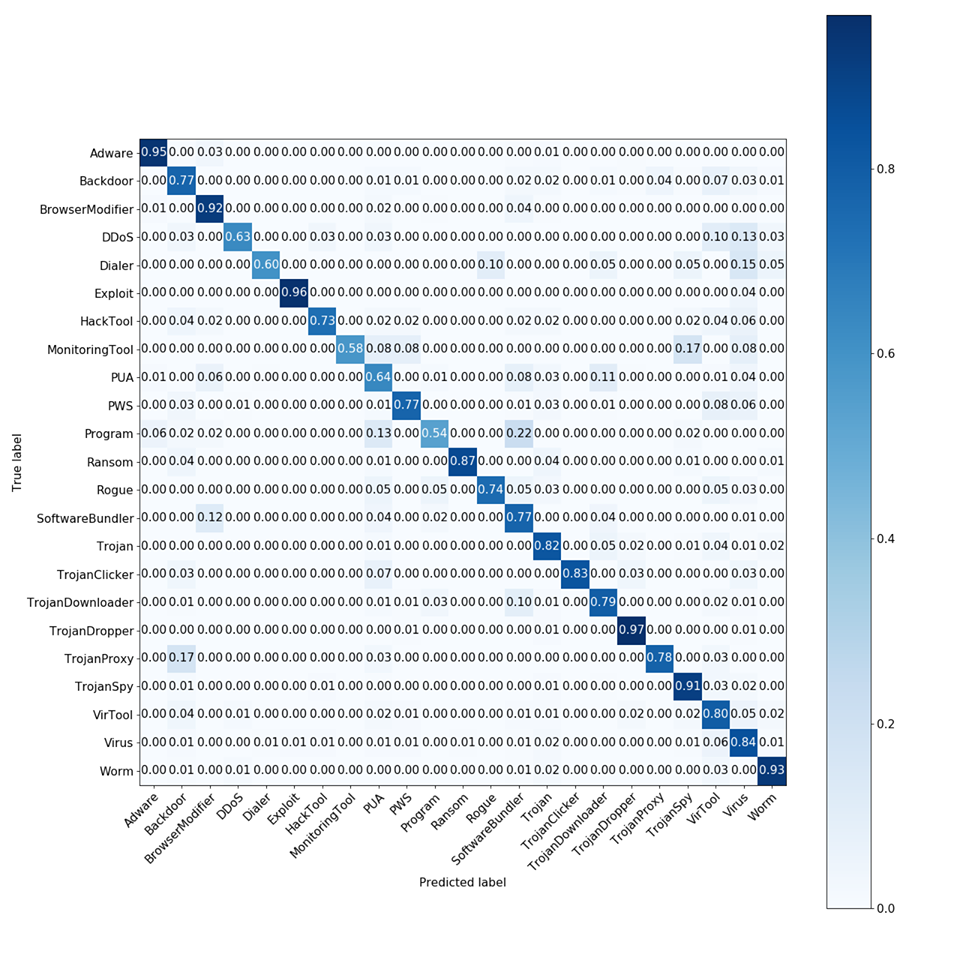
| Scientific Breakthrough | Proposed system uses the architecture of SIEM and uses correlation analysis and artificial intelligence that can reach |
||
| Industrial Applicability | Using artificial intelligence and correlation analysis to capture the signature of the host behavior, the suspicious host and behaviors can be found in the early stage of the attack. Reduce the cost of human and financial after the attack were captured. Proposed system can be applied to campus networks, corporate networks, government networks. |
||
| Keyword | AI Machine Learning Malware Log Behavior Associative Analysis Cluster Analysis Network Flow SIEM Suspicious Target | ||
- tsca@twisc.ncku.edu.tw
other people also saw